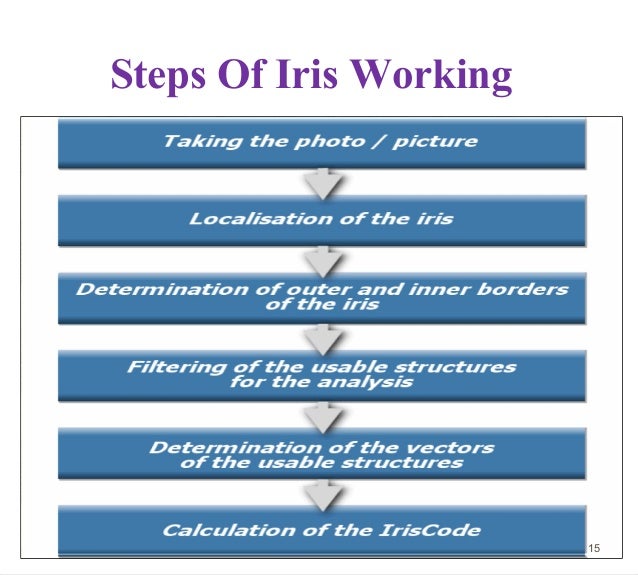
This technique proposes an automatic tellermachine security model that would combine a physical access card, a PIN, andelectronic facial recognition. By forcing the ATM to match a live image of acustomer’s face with an image stored in a bank database that is associated withthe account number, the damage to be caused by stolen cards and PINs iseffectively neutralized. Only when the PIN matches the account and the live image and stored imagematch would a user be considered fully verified. We will also look into an automatic tellermachine security model providing the customers a card less, password-free way to get their money out ofan ATM. Just step up to the camera whileyour eye is scanned. The iris the colored part of the eye the camera will bechecking - is unique to every person, more so than fingerprints.
The first ATMs were off-linemachines, meaning money was not automatically withdrawn from an account. Thebank accounts were not (at that time) connected by a computer network to theATM.
Therefore, banks were at first very exclusive about who they gave ATMprivileges to. Giving them only to credit card holders (credit cards were usedbefore ATM cards) with good banking records. In modern ATMs,customers authenticate themselves by using a plastic card with a magneticstripe, which encodes the customer's account number, and by entering a numeric passcode called a PIN (personal identification number), which in some cases may bechanged using the machine. Typically, if the number is entered incorrectlyseveral times in a row, most ATMs will retain the card as a security precautionto prevent an unauthorized user from working out the PIN by Traditionally, security is handled byrequiring the combination of a physical access card and a PIN or other passwordin order to access a customer’s account. Our ATM system would only attempt to match twodiscrete images, searching through a large database of possible matchingcandidates would be unnecessary. The process would effectively become an exercisein pattern matching, which would not require a great deal of time. Withappropriate lighting and robust learning software, slight variations could beaccounted for in most cases.
Betaal Pachisi is an Indian television series based on the comic strip The Phantom. The 49-episode Hindi series originally ran from 1997 to 1998 on DD National. It was directed by Sunil Agnihotri and starred Shahbaz Khan, Sonu Walia, Puneet Issar, Tom Alter and Vindu Dara Singh. %20back-1000x1000-803x800.jpg)
Further, a positive visual match would cause thelive image to be stored in the database so that future transactions would havea broader base. In addition, ATMs are moving away from custom circuitboards and into full-fledged PCs with commodity operating systems such asWindows 2000 and Linux. An exampleof this is Banrisul, the largest bank in the South of Brazil, which hasreplaced the MS-DOS operating systems in its automatic teller machines withLinux. Other platforms include RMX 86, OS/2 and Windows 98 bundled with Java.The newest ATMs use Windows XP or Windows XP embedded.For most of the past ten years, the majority of ATMs used worldwide ran underIBM’s now-defunct OS/2. However, IBM hasn’t issued a major update to theoperating system in over six years. Movement in the banking world is now goingin two directions: Windows and Linux.
NCR, a leading world-wide ATMmanufacturer, recently announced an agreement to use Windows XP Embedded in itsnext generation of personalized ATMs.Windows XP Embedded allows OEMs to pick and choose from the thousands ofcomponents that make up Windows XP Professional, including integratedmultimedia, networking and database management functionality. This makes theuse of off-the-shelf facial recognition code more desirable because it couldeasily be compiled for the Windows XP environment and the networking anddatabase tools will already be in place. Scientists haveidentified 250 features unique to each person's iris - compared with about 40for fingerprints - and it remains constant through a person's life, unlike avoice or a face. Fingerprint and hand patterns can be changed throughalteration or injury. The iris is the best part of the eye to use as aidentifier because there are no known diseases of the iris and eye surgery isnot performed on the iris.
Iris identification is the most secure, robust andstable form of identification known to man. It is far safer, faster, moresecure and accurate than DNA testing. Even identical twins do not haveidentical irises. The iris remains the same from 18 months after birth untilfive minutes after death.
Whenthe system is fully operational, a bank customer will have an iris record madefor comparison when an account is opened. The bank will have the option ofidentifying either the left or right eye or both. It requires no interventionby the customer. They will simply get a letter telling them they no longer haveto use the PIN number. And, scam artists beware, a picture of the card holderwon't pass muster.
The first thing the camera will check is whether the eye ispulsating. If we don't see blood flowing through your eye, you're either deador it's a picture. In spite of all these security features,a new technology has been developed. Bank United of Texas became the first in the United States tooffer iris recognition technology at automatic teller machines, providing thecustomers a card less and password-free way to get their money out of an ATM.There's no card to show, there's no fingers to ink, no customer inconvenienceor discomfort.
It's just a photograph of a Bank United customer's eyes. Juststep up to the camera while your eye is scanned.
An Atm With An Eye Pdf Free Download
The iris - the colored partof the eye the camera will be checking - is unique to every person, more sothan fingerprints. And, for the customers who can't remember their personalidentification number or password and scratch it on the back of their cards orsomewhere that a potential thief can find, no more fear of having an accountcleaned out if the card is lost or stolen. Deployedapplications:. Aadhar,India's UID project uses Iris scan along with fingerprints to uniquelyidentify people and allocate a Unique Identification Number. Police forces across America plan to start using BI2Technologies’ mobile MORIS (Mobile Offender Recognition and InformationSystem)in 2012. New York City Police Department was the first, installedin Manhattan fall of 2010. At, iris recognition has permitted passport-freeimmigration since 2001.
uses iris scanners to control access to their. On May 10, 2011, Hoyos Group demonstrated a devicecalled EyeLock using iris-recognition as an alternative to passwords tolog people in to password-protected Web sites and applications, likeFacebook or eBay. The iris of the eye has beendescribed as the ideal part of the human body for biometric identification forseveral reasons:.


It is an internal organ that is well protected againstdamage and wear by a highly transparent and sensitive membrane (the ).This distinguishes it from fingerprints, which can be difficult torecognize after years of certain types of manual labor. The iris is mostly flat, and its geometricconfiguration is only controlled by two complementary muscles (thesphincter pupillae and dilator pupillae) that control the diameter of thepupil. This makes the iris shape far more predictable than, for instance,that of the face. The iris has a fine texture that—like fingerprints—isdetermined randomly during embryonic. Like the fingerprint, it is very hard (if notimpossible) to prove that the iris is unique. However, there are so manyfactors that go into the formation of these textures (the iris andfingerprint) that the chance of false matches for either is extremely low.Even genetically identical individuals have completely independent iristextures.
An iris scan is similar to taking a photograph and canbe performed from about 10 cm to a few meters away. There is no needfor the person being identified to touch any equipment that has recentlybeen touched by a stranger, thereby eliminating an objection that has beenraised in some cultures against fingerprint scanners, where a finger hasto touch a surface, or retinal scanning, where the eye must be broughtvery close to an eyepiece (like looking into a microscope). Interms of the improvement of security standards, MasterCard is spearheading aneffort to heighten the encryption used at ATMs. For the past few decades, manymachines have used the Data Encryption Standard developed by IBM in the mid1970s that uses a 56-bit key. DES has been shown to be rather easily cracked,however, given proper computing hardware. In recent years, a “Triple DES”scheme has been put forth that uses three such keys, for an effective 168-bitkey length.
ATM manufacturers are now developing newer models that supportTriple DES natively; such redesigns may make them more amenable to also includingsnapshot cameras and facial recognition software, more so than they would be inregards to retrofitting pre-existing machines. Because the system would only attempt tomatch two (and later, a few) discrete images, searching through a largedatabase of possible matching candidates would be unnecessary. The processwould effectively become an exercise in pattern matching, which would notrequire a great deal of time. With appropriate lighting and robust learningsoftware, slight variations could be accounted for in most cases. Further, a positivevisual match would cause the live image to be stored in the database so thatfuture transactions would have a broader base from which to compare if theoriginal account image fails to provide a match – thereby decreasing falsenegatives.
An Atm With An Eye Pdf
We thus develop an ATM model that is morereliable in providing security by using facial recognition software. By keepingthe time elapsed in the verification process to a negligible amount we even tryto maintain the efficiency of this ATM system to a greater degree. One couldargue that having the image compromised by a third party would have far lessdire consequences than the account information itself. Furthermore, sincenearly all ATMs videotape customers engaging in transactions, it is no broadleap to realize that banks already build an archive of their customer images,even if they are not necessarily grouped with account information.